A Technical Solutions Guide For Privileged Password And Session Management Use Cases
By BeyondTrust
Added
Despite the number of data breach stories in the news, many IT organizations fall into the easy trap of using shared accounts for users, administrators, or applications. While this practice means that, when access is needed, everyone can easily pitch in to get the work done, it comes with massive, unjustifiable security and compliance tradeoffs. This paper seeks to provide assistance with these situations.
Tags
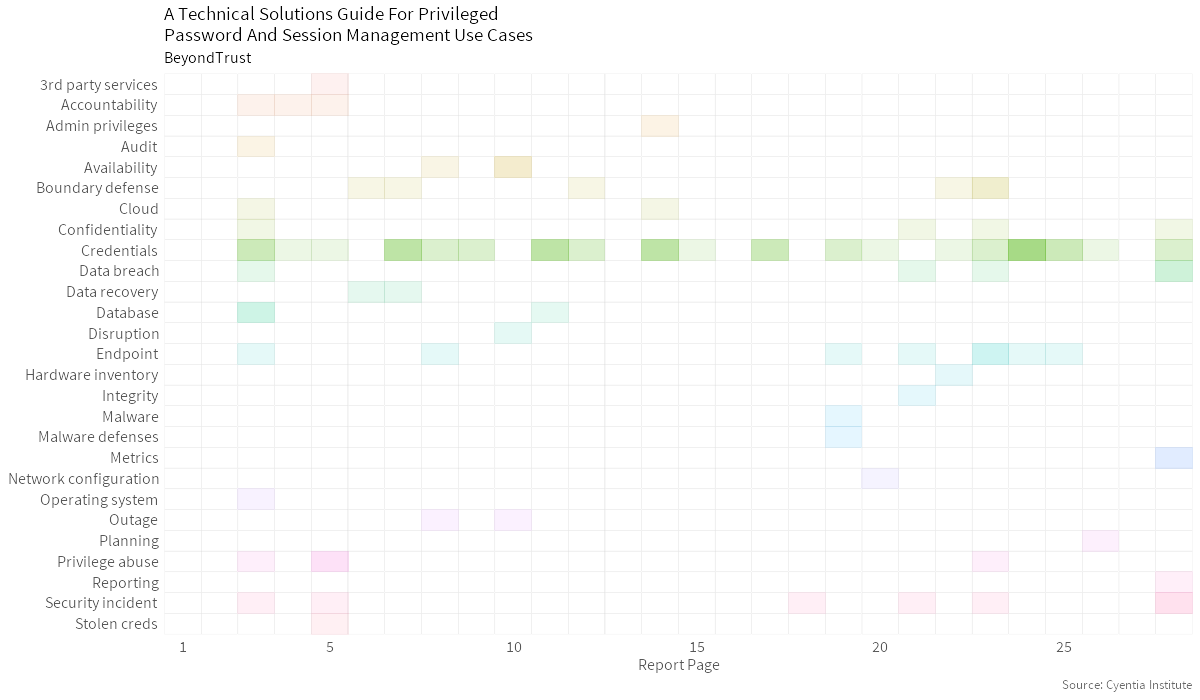
Credentials Endpoint Security Incident Boundary Defense Data Breach Confidentiality Privilege Abuse Accountability Availability DatabaseTopic Map