Behind The Hidden Conversion Of Electricity To Money: An In-Depth Analysis of XMR Cryptominer Malware
By CyberArk
Added
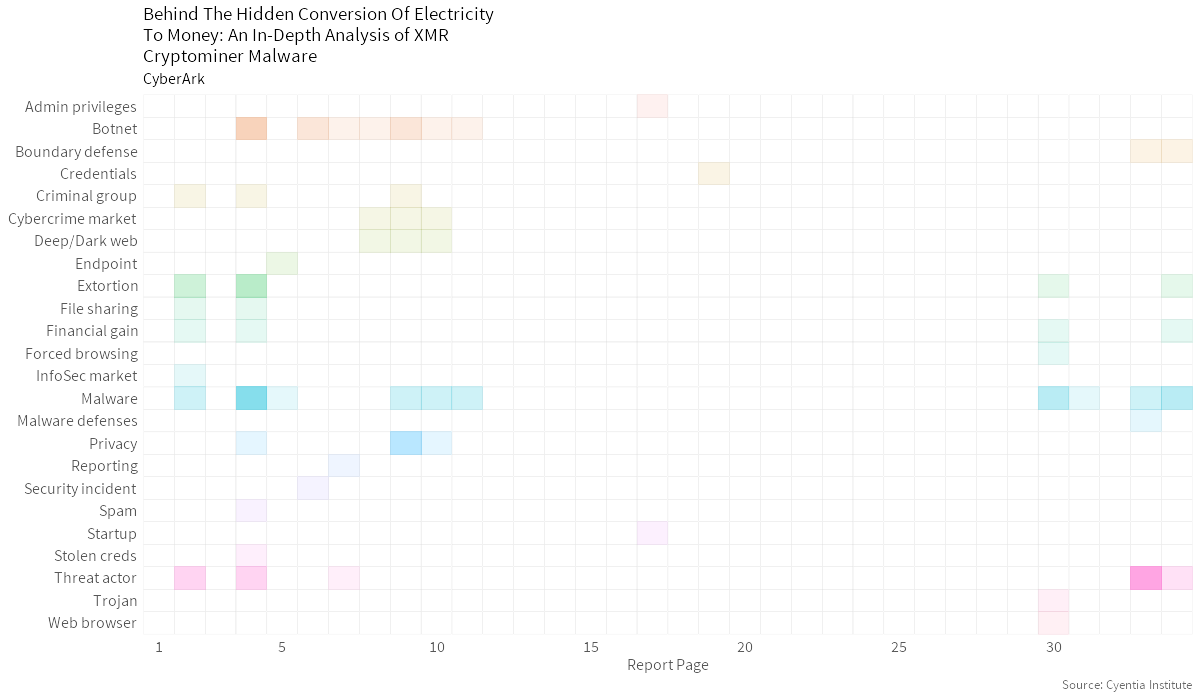
This paper provides an in-depth look at current cryptominer trends and the technology behind Monero. Additionally, it explores the projected attack methods that threat actors are likely to adopt, as well as tactics and best practices that security teams can utilize to keep themselves on the right side of this emerging cat-and-mouse game.
Tags
Malware Threat Actor Botnet Extortion Privacy Financial Gain Criminal Group Cybercrime Market Deep/Dark Web Boundary DefenseTopic Map