2015 Strategic Security Survey
By Informationweek / Dark Reading
Added
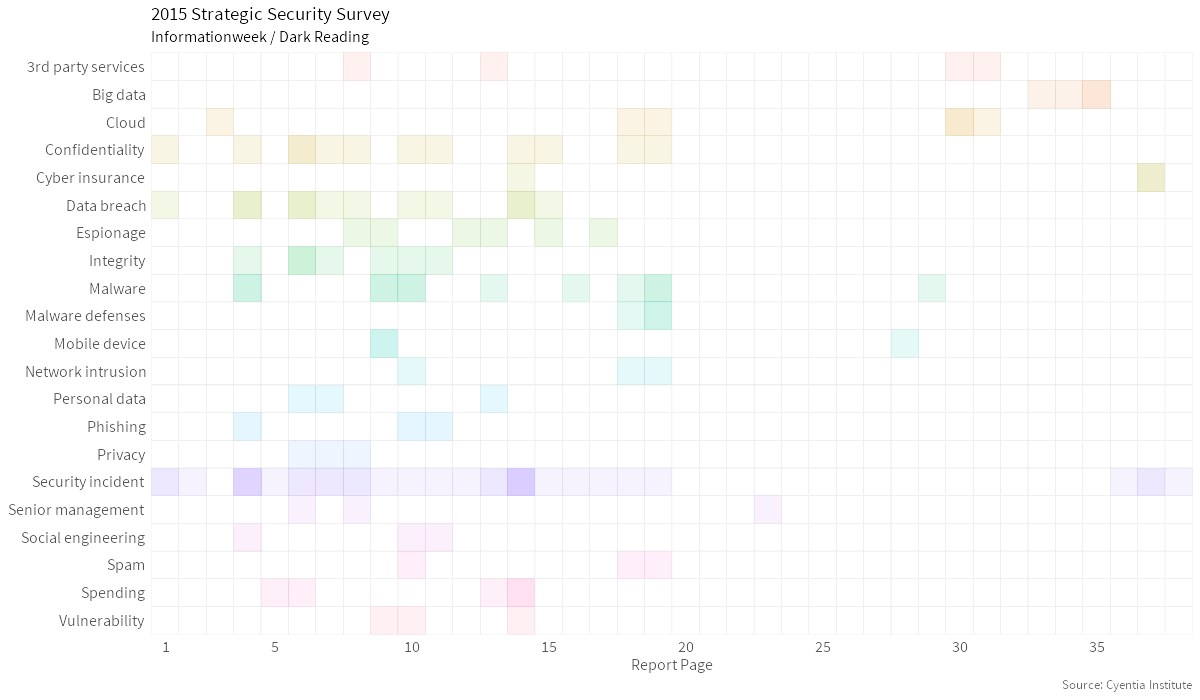
In this report, they: a) Discuss the assumptions shaping IT defense spending plans b) Delve into the real and intangible costs of a data breach c) Examine why malware is still the most common form of breach. d) Look at which threats on which security teams need to focus.
Tags
Security Incident Confidentiality Data Breach Malware Integrity Cloud Espionage Spending 3rd Party Services Big DataTopic Map