2015 Threats Report
By McAfee
Added
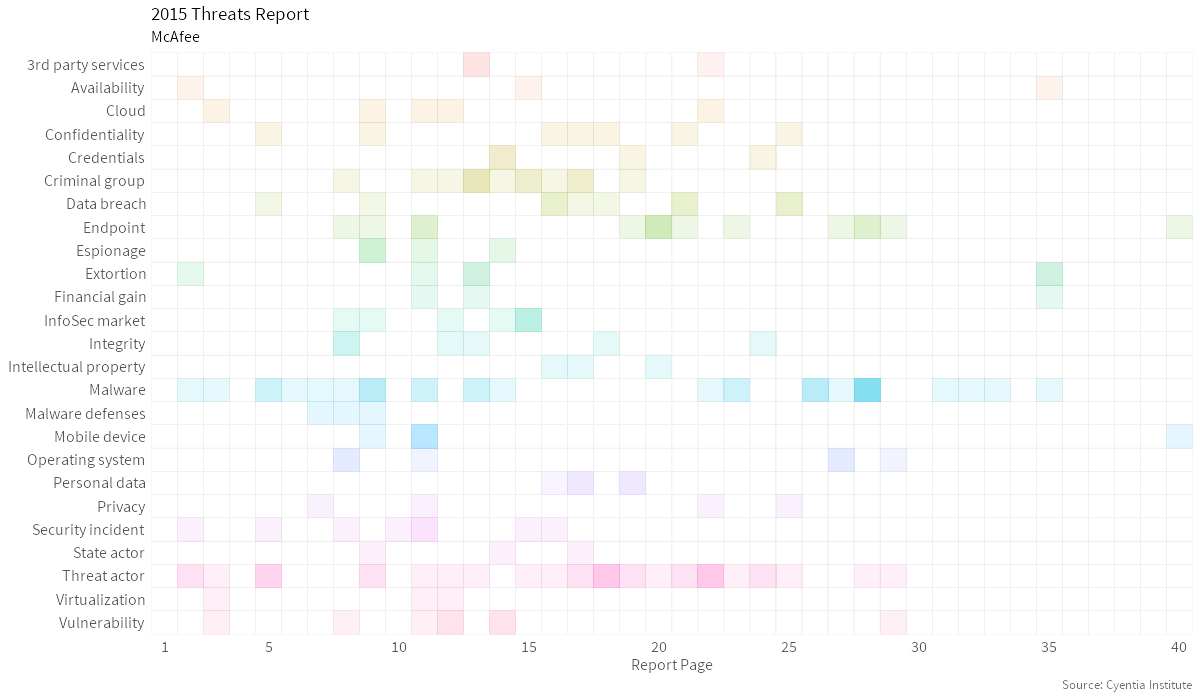
In this report, McAfee looks back on the past 5 years of cyber threats. They then breakdown two key points, 1) How do attackers enter a malware infected system and exfiltrate information and 2) Cyber attacks on graphic processing units and (GPU) devices.
Tags
Threat Actor Malware Endpoint Criminal Group Data Breach Security Incident Vulnerability Confidentiality InfoSec Market ExtortionTopic Map